Keytool.
Information
A keystore is a password-protected file which stores the keys and certificates.
The keytool application can import, export and list the contents of a keystore.
The keytool can also be used to generate self-signed certificates for test purposes.
The keytool use as default a keystore file ".keystore" which is located
in your home directory or profile directory (C:\Documents and Settings\MyName) for Windows XP.
To use another keystore file use the -keystore flag.
To list the content of a keystore, type:
keytool -list
When referring to a particular entity in the keystore use the -alias flag.
Certificates generated by the system will be valid for just under one year by default.
To change the length of validity for a certificate to n days, add the flag -validity
More information about the keytool at:
http://java.sun.com/j2se/1.4.2/docs/tooldocs/windows/keytool.html
Operating system used
Windows XP Home Edition Version 5.1 SP 2
Software prerequisites
Java 2 Standard Edition (J2SE) SDK, version 1.4 or higher.
Procedure
- Generating an RSA keypair and self-signed certificate can be performed
from the command line in one shot.
With this keypair, an RSA-Signed Certificate can be created to sign applets.
- Generate an RSA keypair:
- Create two directories:
- C:\mykeytools
- C:\mykeytools\keys
- Goto directory C:\mykeytools
- Type:
keytool -genkey -alias myalias -keyalg RSA -validity 365 -keystore keys/my.keystore
- Enter keystore password: mysecret
What is your first and last name?
[Unknown]: www.mobilefish.com
What is the name of your organizational unit?
[Unknown]:Research and Development
What is the name of your organization?
[Unknown]: Mobilefish.com
What is the name of your City or Locality?
[Unknown]: Zaandam
What is the name of your State or Province?
[Unknown]: Noord-Holland
What is the two-letter country code for this unit?
[Unknown]: NL
Is CN=www.mobilefish.com, OU=Research and Development, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL correct?
[no]: y
Enter key password for <myalias>
(RETURN if same as keystore password):
- File C:\mykeytools\keys\my.keystore is created.
- To view the fingerprints of certificates in the keystore, type:
keytool -list -keystore keys/my.keystore
You should see and do the following:
Enter keystore password: mysecret
Keystore type: jks
Keystore provider: SUN
Your keystore contains 1 entry
myalias, 18-mei-2005, keyEntry,
Certificate fingerprint (MD5): D5:14:AB:F5:68:4B:1F:C9:80:8C:3E:95:D7:4D:E1:0E
- To view the personal information about the issuer and owner of the certificate, type:
keytool -list -v -keystore keys/my.keystore
You should see and do the following:
Enter keystore password: mysecret
Keystore type: jks
Keystore provider: SUN
Your keystore contains 1 entry
Alias name: myalias
Creation date: 18-mei-2005
Entry type: keyEntry
Certificate chain length: 1
Certificate[1]:
Owner: CN=www.mobilefish.com, OU=Research and Development, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Issuer: CN=www.mobilefish.com, OU=Research and Development, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Serial number: 428b9752
Valid from: Wed May 18 21:28:18 CEST 2005 until: Thu May 18 21:28:18 CEST 2006
Certificate fingerprints:
MD5: D5:14:AB:F5:68:4B:1F:C9:80:8C:3E:95:D7:4D:E1:0E
SHA1: 88:BA:32:2C:DD:45:62:5B:48:8A:2D:C0:AC:9F:79:AA:CB:09:B8:5D
- To export the certificate stored in the keystore to a certificate file mycert.cer, type:
keytool -export -alias myalias -file mycert.cer -keystore keys/my.keystore
- To remove entries from the keystore, enter the following command:
keytool -keystore keys/my.keystore -delete -alias myalias
You should see and do the following:
Enter keystore password: mysecret
Note: In this example a key entry with alias name "myalias" is removed.
- Once a private key has been generated, jarsigner can be used to mark a JAR file with the public key
of the signer, type:
jarsigner -verbose -keystore keys/my.keystore -signedjar my_signed.jar my_unsigned.jar myalias
You should see and do the following:
Enter Passphrase for keystore: mysecret
updating: META-INF/MANIFEST.MF
adding: META-INF/MYALIAS.SF
adding: META-INF/MYALIAS.RSA
signing: DisplaySystemProperties.class
- To verify if a jar file is signed, type:
jarsigner -verify -verbose -certs signed.jar
You should see the following:
153 Wed May 18 21:37:10 CEST 2005 META-INF/MANIFEST.MF
206 Wed May 18 21:37:10 CEST 2005 META-INF/MYALIAS.SF
996 Wed May 18 21:37:10 CEST 2005 META-INF/MYALIAS.RSA
0 Sat May 14 16:11:10 CEST 2005 META-INF/
sm 999 Sat May 14 16:10:42 CEST 2005 DisplaySystemProperties.class
X.509, CN=www.mobilefish.com, OU=Research and Development, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
s = signature was verified
m = entry is listed in manifest
k = at least one certificate was found in keystore
i = at least one certificate was found in identity scope
jar verified.
If a jar file is not signed an java.lang.IllegalStateException is thrown due to a bug:
jarsigner: java.lang.IllegalStateException: zip file closed
If an applet is signed and uploaded along with the HTML document to a web server,
you should see a message similar to this when the page that contains the applet is requested:
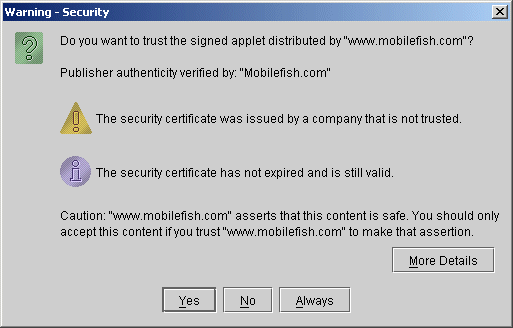
When you click on the "More Details" button, you should see the following:
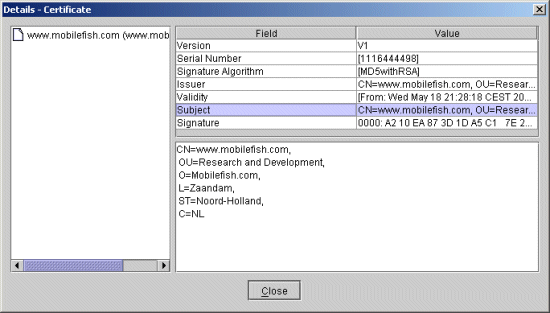
Click on "Yes" and your applet should work without a warning screen displaying.
The two screendumps shown above are actually Java Plug-In Control Panel displays:
- Go to the Windows Control Panel (Start > Run > Control)
- Double click the Java Plug-In icon.

- Select tab Certificates.
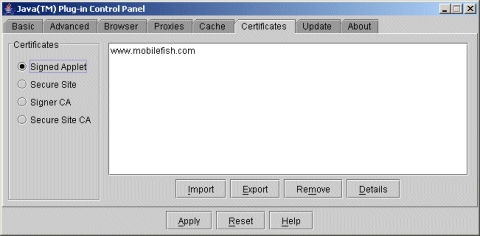
- Select radio button: Signed Applet
- Select certificate: www.mobilefish.com
- Press button Details. You should see the certificate details.
- You can also remove the certificate by pressing the Remove button.
- To avoid the warning screen "Warning - Security" from appearing when the applet is loading,
you must generate a certification signing request and send it to a
trusted Certificate Authority (CA).
To generate a certification signing request, type:
keytool -certreq -keystore keys/my.keystore -alias myalias -file storereq.pem
You should see and do the following:
Enter keystore password: mysecret
- The certificate request file storereq.pem is created.
- The content of the storereq.pem file must be submitted to the CA (e.g. VeriSign/Thawte) for signing.
How it is done will vary and is not described in this guide.
It is then up to the CA to return the certificate data.
-
If you want to know how to create your own CA and sign your certificate request, see guide
"How to sign a certificate request by you own CA".
When you followed the guide, the certificate file C:\Tools\OpenSSL\bin\cert.p7c,
signed by your own CA is created.
You also need your own created CA certificate cacert.pem.
See quick guide "Create your own Root Certification Authority (CA) certificate".
- Copy file cert.p7c and cacert.pem into C:\mykeytools\keys\
ATTENTION: Your own created CA certificate (cacert.pem),
and the certificate signed by your own CA (cert.p7c)
should not be applied on publically accessible sites. Web visitors will still see a warning message
when the applet is loaded, because your own created CA certificate is not
a trusted Certificate Authority.
You can use these certificates on intranet sites or sites only accessible for restricted users.
Below is a list of trusted CA.
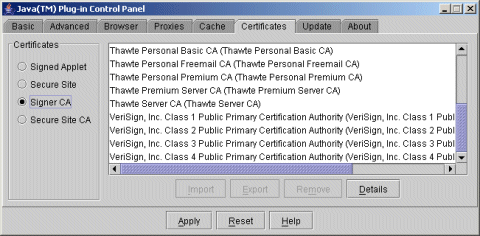
For **test purposes**, you can manually add your own root CA certificate to this list.
This is done as follow:
- First locate the cacerts file which stores the certificates (which include the public keys)
for known and trusted Certificate Authorities. The default location for this file is:
<jre location>\lib\security\cacerts.
The default keystore password for the cacerts file is "changeit".
While the documentation recommends that system administrators change the access
rights and the password for the cacerts file, this password will probably work
on developer or testing machines.
To display the content of this keystore:
keytool -list -v -keystore
"C:\Program Files\Java\j2re1.4.2_01\lib\security\cacerts"
You should see and do the following:
Enter keystore password: changeit
A list of trusted CA certificates are shown.
- To import your own certificate as a trusted CA certificate:
keytool -import -alias rsatest -file cacert.pem -trustcacerts -keystore "C:\Program Files\Java\j2re1.4.2_01\lib\security\cacerts"
You should see and do the following:
Enter keystore password: changeit
Owner: EMAILADDRESS=contact@mobilefish.com, CN=Mobilefish.com CA,
OU=Certification Services, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Issuer: EMAILADDRESS=contact@mobilefish.com, CN=Mobilefish.com CA,
OU=Certification Services, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Serial number: 0
Valid from: Sun Dec 05 19:33:15 CET 2004 until: Sat Nov 30 19:33:15 CET 2024
Certificate fingerprints:
MD5: F4:00:CE:58:AA:E3:88:50:F7:41:44:BF:AE:F2:08:C7
SHA1: CC:DD:9F:D2:AD:B4:B7:D4:ED:0A:6A:73:02:E7:A4:40:26:8A:BB:2A
Trust this certificate? [no]: y
Certificate was added to keystore
In the Java Plug-In Control Panel you can verify if our created CA certificate is added.
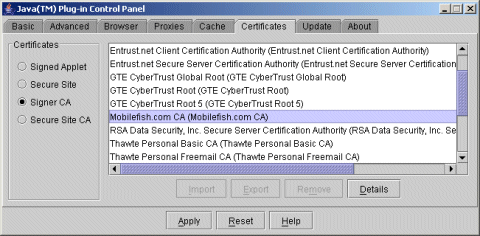
- To remove this certificate:
keytool -keystore "C:\Program Files\Java\j2re1.4.2_01\lib\security\cacerts" -delete -alias rsatest
You should see and do the following:
Enter keystore password: changeit
|
- Import your certificate cert.p7c (signed by your own CA) into your keystore:
keytool -import -keystore keys/my.keystore -alias myalias -trustcacerts -file cert.p7c
ATTENTION:
You must use the same alias name as you did when you created the certification signing request (=myalias)!
You should see and do the following:
Enter keystore password: mysecret
Certificate reply was installed in keystore
The message "Certificate reply was installed in keystore" will only be displayed
if you previously imported your CA certificate in the cacerts keystore.
If you have not done this, the following message will be displayed:
Owner: EMAILADDRESS=contact@mobilefish.com, CN=Mobilefish.com CA,
OU=Certification Services, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Issuer: EMAILADDRESS=contact@mobilefish.com, CN=Mobilefish.com CA,
OU=Certification Services, O=Mobilefish.com, L=Zaandam, ST=Noord-Holland, C=NL
Serial number: 0
Valid from: Sun Dec 05 19:33:15 CET 2004 until: Sat Nov 30 19:33:15 CET 2024
Certificate fingerprints:
MD5: F4:00:CE:58:AA:E3:88:50:F7:41:44:BF:AE:F2:08:C7
SHA1: CC:DD:9F:D2:AD:B4:B7:D4:ED:0A:6A:73:02:E7:A4:40:26:8A:BB:2A
... is not trusted. Install reply anyway? [no]: y
Certificate reply was installed in keystore
- With the jarsigner tool, you can now sign JAR files with the public key which is included in
the certificate storecert.pem.
jarsigner -verbose -keystore keys/my.keystore -signedjar my_signed.jar my_unsigned.jar myalias
As an example you should see and do the following:
Enter Passphrase for keystore: mysecret
updating: META-INF/MANIFEST.MF
adding: META-INF/MYALIAS.SF
adding: META-INF/MYALIAS.RSA
signing: xxx.class
signing: xxx.class
signing: xxx.png
- As an example the MobileStatus applet is signed.
Demonstrate the MobileStatus signed applet.
- To change the password of a keystore:
keytool -storepasswd -keystore keys/my.keystore
Enter keystore password: mysecret
New keystore password: mybigsecret
Re-enter new keystore password: mybigsecret
|