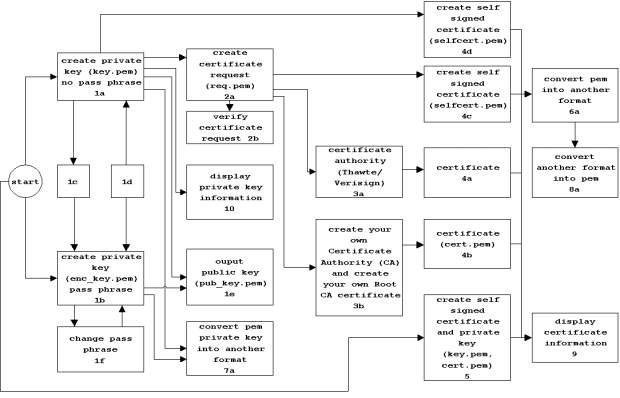
The OpenSSL Project has developed a open source toolkit implementing the
Secure Sockets Layer (SSL v2/v3) and Transport Layer Security TLS (v1)
protocols as well as a full-strength general purpose cryptography library.
OpenSSL is based on the SSLeay library developed by Eric A. Young and
Tim J. Hudson. The OpenSSL toolkit is licensed under an Apache-style licence,
which basically means that you are free to get and use it for commercial
and non-commercial purposes subject to some simple license conditions.
The OpenSSL toolkit can be used to generate the keys that a web server (e.g. Apache) needs
to encrypt the data sent between the client (browser) and the web server.
A simple overview of this process can be found here below:
- A client browser connects to the Apache HTTP server via a Web request.
- The browser asks to start a secure session with the server.
- The server returns the site's certificate (= mobilefish.com_cert.pem) which also includes the server public key.
- The browser analyzes the certificate and informs the user about its validity (e.g.,
was it issued by a recognized, trusted certificate authority?).
- The browser creates a session key, which is encrypted with the server's public key, which is then sent to the server.
This public or asymmetric key is generally 1024 bits.
Much stronger public keys of 2048 bits could be provided but, perhaps for performance reasons,
these are not in general use.
- The server then decrypts this information using its private key (mobilefish.com_key.pem).
- Both the browser and the server now are using the same session key.
This is a symmetric key used to encrypt and decrypt data exchanged by the browser and server.
Browsers and servers usually negotiate the strongest mutually supported session. This means that if
the user's browser and your Web server both support 128-bit SSL sessions, a 128-bit session is established.
If the user's browser only supports 40-bit SSL sessions, then a 40-bit session is
established even if your Web server supports 128-bit sessions.
More information about the OpenSSL Project can be found at:
http://www.openssl.org
The latest OpenSSL version (no binary distributions) can be downloaded from:
http://www.openssl.org/source/
Links to OpenSSL binary distributions can be found at:
http://www.openssl.org/related/binaries.html
|