The OpenSSL Project has developed a open source toolkit implementing the
Secure Sockets Layer (SSL v2/v3) and Transport Layer Security TLS (v1)
protocols as well as a full-strength general purpose cryptography library.
OpenSSL is based on the SSLeay library developed by Eric A. Young and
Tim J. Hudson. The OpenSSL toolkit is licensed under an Apache-style licence,
which basically means that you are free to get and use it for commercial
and non-commercial purposes subject to some simple license conditions.
The OpenSSL toolkit can be used to generate the keys that a web server (e.g. Apache) needs
to encrypt the data sent between the client (browser) and the web server.
A simple overview of this process can be found here below:
- A client browser connects to the Apache HTTP server via a Web request.
- The browser asks to start a secure session with the server.
- The server returns the site's certificate (= mobilefish.com_cert.pem) which also includes the server public key.
- The browser analyzes the certificate and informs the user about its validity (e.g.,
was it issued by a recognized, trusted certificate authority?).
- The browser creates a session key, which is encrypted with the server's public key, which is then sent to the server.
This public or asymmetric key is generally 1024 bits.
Much stronger public keys of 2048 bits could be provided but, perhaps for performance reasons,
these are not in general use.
- The server then decrypts this information using its private key (mobilefish.com_key.pem).
- Both the browser and the server now are using the same session key.
This is a symmetric key used to encrypt and decrypt data exchanged by the browser and server.
Browsers and servers usually negotiate the strongest mutually supported session. This means that if
the user's browser and your Web server both support 128-bit SSL sessions, a 128-bit session is established.
If the user's browser only supports 40-bit SSL sessions, then a 40-bit session is
established even if your Web server supports 128-bit sessions.
More information about the OpenSSL Project can be found at:
http://www.openssl.org
The latest OpenSSL version (no binary distributions) can be downloaded from:
http://www.openssl.org/source/
Links to OpenSSL binary distributions can be found at:
http://www.openssl.org/related/binaries.html
Create self signed certificate and private key.
Information
In order for a web server to use SSL a SSL Certificate is required (also known as Web Server
Certificates and Secure Server Certificates). SSL Certificates are installed onto the web server
hosting the particular website and allow access to the security functionality of the web server itself.
You can implement SSL in either 40-bit and 128-bit encryption,
(40-bit and 128-bit refer to the size of the session key). A session key is a
pair of secret words that a server and client share; these keys are used in the
encryption process of every SSL session. Mathematically speaking, the longer
the session key, the harder it is to break the encryption of the SSL session
and read the transmitted data.
Operating system used
Windows XP Home Edition Version 5.1 SP 2
Software prerequisites
OpenSSL v0.9.7d or higher
Procedure
- Open a dos window and goto OpenSSL bin directory:
e.g.: cd C:\Tools\openssl\bin
- Generate a RSA private key:
C:\Tools\OpenSSL\bin>openssl genrsa -out key.pem 1024
You should see and do the following:
Loading 'screen' into random state - done
Generating RSA private key, 1024 bit long modulus
...............+++
.................+++
e is 65537 (0x10001)
|
1024
|
In this example a 1024 bit RSA private key is created.
The private key sizes for SSL must be either 512 or 1024 for compatibility with
certain web browsers. A keysize of 1024 bits is recommended because keys
larger than 1024 bits are incompatible with some versions of Netscape Navigator
and Microsoft Internet Explorer, and with other browsers that use RSA's BSAFE
cryptography toolkit.
|
|
key.pem
|
In this example the private key is called "key.pem".
|
Note: If you want to be more secure, create a 1024 bit key and encrypt it using
the triple-DES cipher. Instead of issuing above command, enter the following:
openssl genrsa -des3 -out enc_key.pem 1024
During creation of the private key you are asked to enter a pass phrase.
- The file C:\Tools\OpenSSL\bin\key.pem is created.
- To view the content of the key.pem:
C:\Tools\OpenSSL\bin>openssl rsa -noout -text -in key.pem
You should see the following:
Private-Key: (1024 bit)
modulus:
00:de:5b:d5:57:3d:ae:81:75:b0:72:b2:1d:9e:7f:
65:0d:86:95:e7:30:a4:d5:73:f1:d4:83:a8:ab:fe:
78:d3:e5:67:80:7a:c9:40:96:f3:b6:e5:30:5c:2a:
9f:7c:b6:c5:2c:07:12:a5:d0:4f:57:4e:76:c3:62:
d0:48:6f:32:81:e2:69:3c:30:0f:a4:49:eb:86:bf:
59:77:17:f0:94:a3:7a:c2:8a:f5:06:39:96:8f:7a:
04:9f:bf:6c:b6:04:ea:63:b0:bb:71:3f:ea:b6:33:
b3:61:c8:b8:4e:83:14:1e:87:fe:05:e8:ba:33:5d:
68:8b:a8:86:32:dc:2e:6f:55
publicExponent: 65537 (0x10001)
privateExponent:
19:7d:9b:9a:71:b6:c4:9e:92:48:c3:c4:83:7c:05:
40:a4:b2:20:9b:c1:f9:ba:5d:f9:c7:d2:19:4d:85:
da:7c:cc:fd:bc:95:bf:b2:ce:63:a4:28:84:18:5a:
ca:38:45:a8:43:73:4e:d0:ef:97:89:a6:31:c5:ed:
2c:b0:9a:b0:74:69:0e:05:de:b1:b5:f0:b9:9c:cb:
f9:c0:26:35:1b:7b:87:a6:93:8a:6c:7c:bf:e4:fe:
d5:aa:60:89:f5:ae:42:d0:07:7b:eb:06:9b:5a:f0:
8f:2d:39:e0:9c:38:65:ed:62:5b:21:75:21:fb:6f:
71:e1:4b:ff:20:8f:81:2d
prime1:
00:ef:ca:19:c3:24:18:1d:a2:c6:6d:5e:24:bc:86:
3c:c0:32:21:72:3f:7c:50:b6:f3:e8:66:de:31:ce:
de:46:48:84:d1:80:a1:b2:8b:06:75:3c:54:ae:05:
21:d2:27:d1:31:d6:92:da:6f:60:5f:62:06:69:c6:
58:e5:c1:88:27
prime2:
00:ed:64:11:a9:da:c3:62:c1:0c:75:5d:67:23:5d:
5a:2e:6e:09:cd:9a:58:f1:a8:a2:04:7d:65:a5:cd:
66:22:30:97:45:a5:99:ef:a0:47:40:f0:37:20:0c:
37:5a:5f:c6:57:79:2d:12:d9:68:f7:c6:7b:f3:9e:
ae:c5:81:de:23
exponent1:
00:ee:90:51:85:35:f9:d0:32:4b:dc:2f:97:b9:00:
8c:9c:62:c3:a7:d8:c5:a3:c0:01:76:2c:31:cf:b8:
12:a8:36:29:fe:0d:4d:d2:46:42:cc:8c:93:6a:f6:
ac:29:5b:77:e3:6f:a9:77:2c:eb:e2:b9:b1:cb:b6:
8c:67:39:5e:6d
exponent2:
55:d3:4e:07:88:ce:07:10:20:7e:f6:2b:e9:bf:40:
71:74:db:1a:78:69:1b:c5:89:fd:f1:90:24:67:a4:
3b:4c:32:04:be:20:6f:60:15:22:c7:36:46:e1:e3:
c9:4a:c3:1c:b0:f4:b8:d1:dd:7f:67:45:3d:08:eb:
cb:00:6e:dd
coefficient:
5c:16:32:f9:53:a3:57:58:0a:c3:ff:13:5e:95:4e:
d8:e1:b2:c6:b6:75:77:54:2e:10:67:c9:9b:5e:ce:
c6:6b:1a:f7:a0:41:9a:92:c2:27:85:4f:d1:01:80:
76:43:73:c9:59:dd:71:ad:84:9f:ff:0b:3c:5c:13:
33:50:c7:39
Note:
The numbers prime1 (p) and prime2 (q) are randomly chosen large prime numbers.
The public modulus (n) is calculated by multiplying the prime numbers n=p*q.
The strength of a RSA key actually refers to the bit length of the public modulus.
The prime numbers should never be disclosed!
The publicExponent (e) is a small randomly chosen integer (in practice is
usually either 3 or 65537) such that it and (p-1)*(q-1) are relatively prime.
Two numbers are relatively prime if they share no factors than one; they may or may not actually be prime.
Using e, p, and q, the value of d is computed.
The n and e members are the public key, and the d member is the private key.
- Create a Certificate Signing Request (CSR) with the RSA private key.
Please note that the following characters can not be accepted:
< > ~ ! @ # $ % ^ * / \ ( ) ? . , &
C:\Tools\OpenSSL\bin>
openssl req -new -key key.pem -out req.pem
You should see the following:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:NL
State or Province Name (full name) [Some-State]:Noord-Holland
Locality Name (eg, city) []:Zaandam
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Mobilefish.com
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []: www.mobilefish.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Note: The Certificate Signing Request (CSR) includes the public key.
|
Country Name
|
The two-letter ISO 3166
abbreviation for your country.
|
|
State or Province Name.
|
The state or province where your organization is legally located. Do not abbreviate.
In this example: Noord-Holland
|
|
Locality Name
|
The city where your organization is legally located. Do not abbreviate.
In this example: Zaandam
|
|
Organization Name
|
The exact legal name of your organization. Do not abbreviate your organization name.
In this example: Mobilefish.com
|
|
Organization Unit Name
|
Section of the organization.
Mobilefish.com does not have any organizational units but in yours it maybe
Marketing, Research and Development, Human Resources, Sales
|
|
Common Name
|
The fully qualified domain name for your web server. This must be an exact match.
In this example the url https://www.mobilefish.com will be used.
The common name must be: www.mobilefish.com
|
|
Email Address
|
Enter your organization general email address.
In this example
|
|
Challenge password and optional company name
|
Leave both fields empty.
|
- The file C:\Tools\OpenSSL\bin\req.pem is created.
- Now create a self signed certificate which means no Root Certificate Authority
has signed this certificate:
C:\Tools\OpenSSL\bin>
openssl req -x509 -key key.pem -in req.pem -out cert.pem -days 365
- The file C:\Tools\OpenSSL\bin\cert.pem is created.
-
The certificate (cert.pem) and private key (key.pem) are now both created and
can be used to setup SSL for the web server.
It is recommended to rename these files:
cert.pem into mobilefish.com_cert.pem
key.pem into mobilefish.com_key.pem
More information on how to setup SSL for Apache 2 on Windows XP.
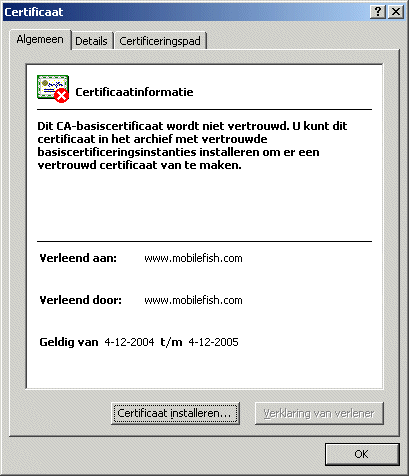
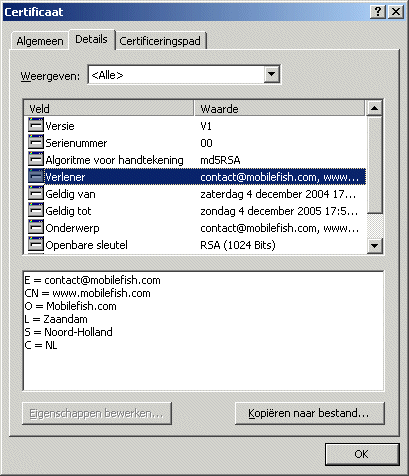
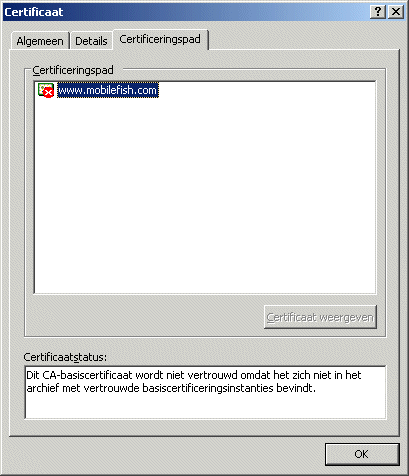
To give you a preview of how the self signed certificate looks like:
Unfortunately all text are in ducth.
- Instead of using the OpenSSL tool, Mobilefish.com provides a free service to
create self-signed SSL certificates online.
|
|


